Taking eFPGA Security to the Next Level
By Ralph Grundler, Flex Logix Technologies, Inc. and Vincent van der Leest, Intrinsic ID B.V.
Many markets – 5G, networking, cloud storage, defense, smart home, automotive, and others – are looking to embedded FPGAs (eFPGA) to save power and reduce cost. By removing the high-speed SERDES and other unnecessary I/Os or unused peripherals, port the design to a smaller process node, move fixed parts of the design to the SOC, the customer can save power and reduce latency. With FPGA embedded, the end product can take advantage of these benefits and still be reconfigurable in the field, saving time and money.
eFPGA vendor because of strong adoption based on several patented technologies that reduce the size of the eFPGA. One of these technologies is the Boundless Radix Interconnect technology, which can reduce the interconnect area by forty-five percent (Fig 1). This results in an area efficient solution, similar in density as custom designed FPGA chips while offering higher utilization and using just the lower layers in a metal stack making it compatible with most metal stacks. question of security is being raised, and it’s an important one.
Bitstream Encryption to Protect eFPGAs
Security is an important topic for every SOC, but it’s especially salient in the context of high- risk assets included in the eFPGA for obfuscation. Whether the device is used in defense systems or in cars driving around town, encryption is important so the device remains secure and can’t be modified maliciously, whether through physical attacks or remote hacking.
Reconfigurability has many uses, but in the past, this meant greater area and came at an additional cost that was difficult to justify except where it was a requirement. Smaller technology nodes and the increasing cost of taping out (or retaping out), have made FPGA technology from Flex Logix, EFLX® eFPGA, both simple to integrate using less area than ever before and easy to justify from a cost perspective.
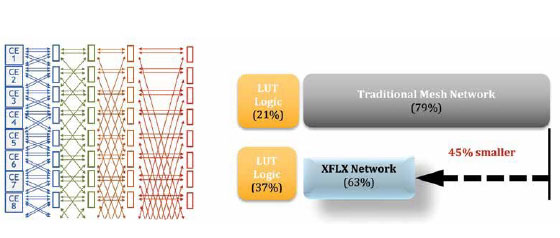
Flex Logix has become the number one
eFGPA adoption has been strong in several markets. Like many new technologies, the adoption started out in defense and aeronautical applications by AFRL, Boeing and DARPA. Next came technologies that require reconfigurability but needed to save power: 5G, Vehicle to Vehicle communication, software defined radio, smartNICs and computational storage and the final adopters are consumer products who require a much lower power and cost. As more and more SOCs are integrating FPGAs, the
But before eFPGA fabric can be used for security purposes, you first need to make sure that whatever is loaded onto this fabric can be trusted. That is why the most important security measure that needs to be implemented for eFPGAs is bitstream encryption. The bitstream, which determines the functionality of the programmable fabric, is typically stored persistently in non-volatile memory (NVM) somewhere internal or external to the SOC. When the device is powered, this bitstream is loaded from the NVM onto the programmable fabric for the eFPGA to become operational. The bitstream contains all the user configuration data and any user data, which should clearly never be altered or stolen. This means that eFPGAs present a unique security challenge, because the bitstream is vulnerable to attack, both when residing in NVM and during transfer. It should never be possible to copy this data to another device to make counterfeit products or make malicious alterations to influence operations of the device.
But what if you could encrypt this eFPGA configuration data with a device-unique key that is never stored on the device, that cannot be copied from one device to the next, and that is not known to anyone (not even you)? Now you can, by using the secure and patented SRAM PUF (or Physical Unclonable Function) technology from Intrinsic ID.
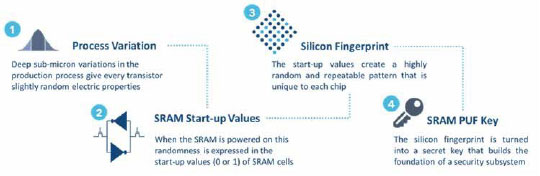
SRAM PUF Technology
A PUF is a physical entity embodied in a physical structure. PUFs utilize deep submicron variations that occur naturally during semiconductor production, and which give each transistor slightly random electric properties – and therefore a unique identity.
Intrinsic ID created SRAM PUF technology, based on the behavior of standard SRAM memory that is available in any digital chip. Every SRAM cell has its own preferred state every time the SRAM is powered, resulting from random differences in the threshold voltages. This randomness is expressed in the startup values of ‘uninitialized’ SRAM memory. Hence an SRAM response yields a unique and random pattern of 0’s and 1’s. This pattern is like a chip’s fingerprint since it is unique to a particular SRAM and hence a particular chip.
Proprietary algorithms turn the device- unique fingerprint into a cryptographic root key for the chip (Fig 2 on previous page). A key that is created using an SRAM PUF is never stored ‘on the chip’ but rather it is extracted ‘from the chip’, only when it is needed. In that way the key is only present in the chip during a very short time window. When the SRAM is not powered there is no key present on the chip making the solution very secure.
This device-unique root key should never be used directly for cryptographic purposes to prevent the risk of exposing this key through use. That is why good cryptographic hygiene prescribes the derivations of additional keys from the root key. This is standard practice for any root key and not specific to SRAM PUFs, so standard algorithms are available for this purpose. What is specific to SRAM PUF technology is that even these derived keys do not require storage in any form of memory. Like the root key, they can simply be regenerated every time they are needed.
Once additional keys have been derived the bitstream of the eFPGA can be encrypted and authenticated. Now if the device is attacked or found in the field, the bitstream of the eFPGA cannot be altered, read, or copied to another device, because it is protected by a key that is never stored and therefore is invisible and unclonable for the attacker.
The main benefits of using the Intrinsic ID SRAM PUF technology over storing a key in NVM are:
- High Security: No key material pro- grammed into device and no key present when it is not in use.
- High Flexibility: Key generation at any time and place in the supply chain without external
- Low Cost: No dedicated security hard-ware required to protect the key, as it is never stored.
- Highly Scalable: It employs only standard logic, scaling effortlessly with shrinking technology
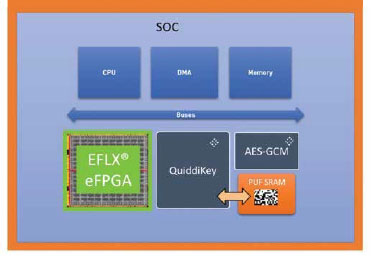
Figure 3: Diagram of QuiddiKey with PUF SRAM implemented in a system with EFLX eFPGA.
Using SRAM PUF Technology with EFLX
From the SOC hardware engineering point of view, the process for encryption with SRAM PUF- based keys is no different than with any other type of encryption. It only requires instantiating the SRAM PUF through the Intrinsic ID hardware IP called QuiddiKey®, which takes care of creating the device-unique root key as well as deriving the additional keys needed to encrypt and authenticate the bitstream. The standard implementation looks like the diagram below (Fig 3).
The system will power up just like any other eFPGA, but the AES-GCM will fetch the key from QuiddiKey and decrypt the eFPGA configuration data before programming the eFPGA in the SOC.
The configuration data can be stored in any unprotected NVM since it is protected by the key from the SRAM PUF.
The use of SRAM PUF technology guarantees that the data used to program the eFPGA can be trusted and that it cannot be reused on malicious or counterfeit devices. This way eFPGA technology can be deployed securely in high-risk assets and in security sensitive markets, such as defense, automotive, and critical infrastructures. This is why the collaboration between Flex Logix and Intrinsic ID offers you everything you need to take your device security to the next level. Contact us now to find out how we can help you by combining eFPGA and SRAM PUF technology.
Learn more about the Flex Logix eFPGA solutions at: https://flex-logix.com/efpga/
Learn more about the Intrinsic ID PUF technology at: https://www.intrinsic-id.com/physical-unclonable-function/

